An interesting article was put out this week on a real-world attack campaign that was detected by the Azure Security Center (ASC) team with some recommendations on how to prevent similar attacks on your environment. I’ve listed some of the simple steps from this article you can perform on your own to prevent the same thing happening to you.
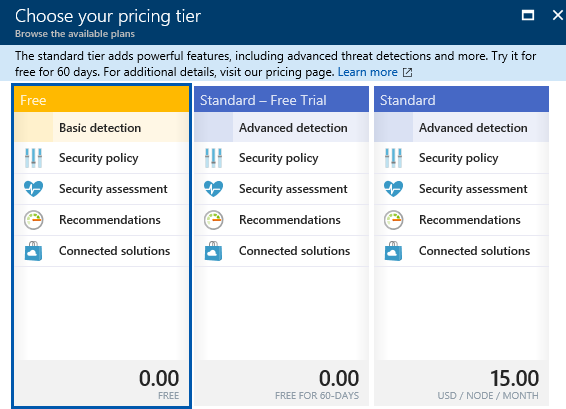
First thing you should do is spend that extra little bit of money (right now $15/month) to configure your Azure subscription(s) to receive alerts and email notifications from the Microsoft Azure Security Center. This involves upgrading from ASC “Free” (basic detection) tier to ASC “Standard” (advanced detection) tier which is a worthwhile cost to protect yourself from such attacks. This Standard tier of Security Center includes:
- Threat intelligence – Looks for known bad actors by using global threat intelligence from Microsoft products and services, the Microsoft Digital Crimes Unit, the Microsoft Security Response Center, and external feeds
- Behavioral analysis – Applies known patterns to discover malicious behavior
- Anomaly detection – Uses statistical profiling to build a historical baseline. It alerts on deviations from established baselines that conform to a potential attack vector
To enable it:
- Select the Policy tile on the Security Center blade.
- Select the subscription that you want to upgrade to Standard.
- On the Security policy blade, select Pricing tier.
- On the Choose your pricing tier blade, select Standard.
- Click Select.
Other precautions the article mentions are as follows:
- Disable ‘sa’ account and use the more secure Windows Authentication for your Azure SQL server instance
- Rename the ‘sa’ account for your Azure SQL server instance
- Ensure that ‘xp_cmdshell’ is disabled
- Configure a Rule to block 1433 in Network Security Group
- Inspect all stored procedures that may have been enabled in SQL and look for stored procedures that may be implementing ‘xp_cmdshell’ and running unusual command
Reference the full article for step by step and screenshots on how to do each step listed above.